home ![]() products
products ![]() pe explorer
pe explorer ![]() feature tour
feature tour
PE EXPLORER: HEADERS INFORMATION VIEWER
Viewing The EXE File Headers (File Header and Optional Header) Information
The Headers Info Viewer provides a default view of the file's contents, showcasing essential information about the executable's headers. This information includes details about the intended machine for execution, the number of sections within the file, the linking time, and whether it is an executable or a Dynamic Link Library (DLL), among other insights.
With the Headers Info Viewer, you can simplify the extensive internal information present in PE files into a more user-friendly format for easy viewing. Additionally, you have the option to save this header information to a text file for reference or documentation purposes.
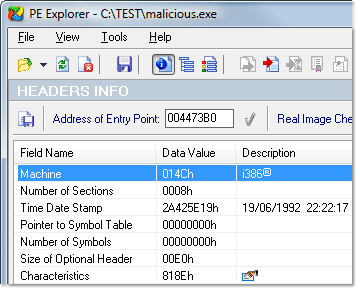 Upon selecting an executable for examination, PE Explorer presents you with comprehensive details about the file's headers – the COFF File Header and the Optional Header. This information includes the number of code sections, the image's size, the application subsystem, and the stack size information.
Upon selecting an executable for examination, PE Explorer presents you with comprehensive details about the file's headers – the COFF File Header and the Optional Header. This information includes the number of code sections, the image's size, the application subsystem, and the stack size information.
The File Header tells on which machine the binary is supposed to run, how many sections are in it, the time it was linked, whether it is an executable or a DLL and so on. In this context, an executable refers to a standalone program that can be run independently, while a DLL is meant to be utilized by another binary and cannot be directly initiated.
The Optional Header, as the name suggests, is not present in all files – it's optional for some types (like object files) but necessary for image files. This header offers more insights into how the binary is to be loaded, such as the starting address, reserved stack size, and data segment size. In addition, it is important to validate the Optional Header’s Magic number to ensure compatibility with the PE32 format.
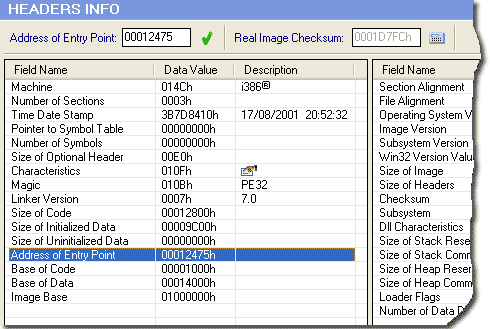
Entry Point Modification
The Entry Point value can be modified using automatic range checking. PE Explorer will notify you if the new value falls outside of the permissable range disabling the button.
Characteristics Editor
Characteristics are a collection of flags. The image characteristics value contains an OR of these flags. This is a way of informing the OS about the certain aspects of the application. For instance, it can be used to tell the OS that the application is ready and compatible with getting access to virtual memory addresses above the 2 GB boundary (Bit 0x0020).
The Characteristics Editor helps you view or set flag bits in the PE file header Characteristics field:
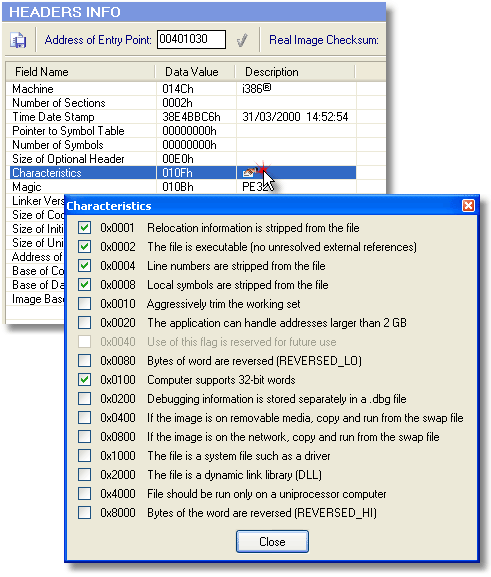
All the flag values are OR'ed (each value is different, so the binary patterns just fall in place with respect to their respective position in order to resemble a composite binary pattern) to get the final value in hexadecimals in order to communicate to the Windows loader of the required values in the binary header field. Some values are of special importance for malware analysis: 0x2000 signifies that the file is a dynamic link library (DLL), and conversely, 0x0002 signifies that the file is an executable (no unresolved external references), which is an EXE file in this instance. 0x1000 would signify that the file is a system file, such as a driver (.sys). The remaining flags are also important, and they convey the validity of the executable to Windows, such as swap file usage if the file image is on removable media or the network, among others.
PE File Checksum
You can compare the real checksum to the value reported by the PE header. If necessary it is possible to update the value of the checksum in the header. Usually compilers do not fill this field, with the exception of NT-drivers. We recommend you use it in writing your own program to verify its own integrity at load time. It will allow you to be relatively sure in the integrity of the code and detect intentional, and even crafty modifications to a file.
The file checksum is computed at opening. It is used in Windows NT for validation at load time: all drivers, any DLL loaded at boot time, and any DLL that ends up in the server are checked. The checksum is supposed to prevent loading of damaged binaries that would crash anyway (a crashing driver would result in a BSOD, so it is better not to load it at all). That is, a checksum is intended to detect simple memory failures leading to corruption (whether or not a block of memory on disk has gone bad and the values stored there have become corrupted). In general, any discrepancies result in discarding the particular instance.
Some Microsoft System DLLs also use the linker checksum to count how many instances of a particular file is loaded. When the limit is reached Windows NT will not under any circumstances load such marked files regardless of admin status etc. Usually no error is reported either just nothing happens after executing a program dependent on one of these libraries. Example is common control library with limit of 32 instances.
See also DLL Export Viewer: Review of the information on entry points, numbers, names and calling syntax of exported functions.
![]() Download a 30 day trial version of PE Explorer
Download a 30 day trial version of PE Explorer ![]() Buy the Full Version
Buy the Full Version
